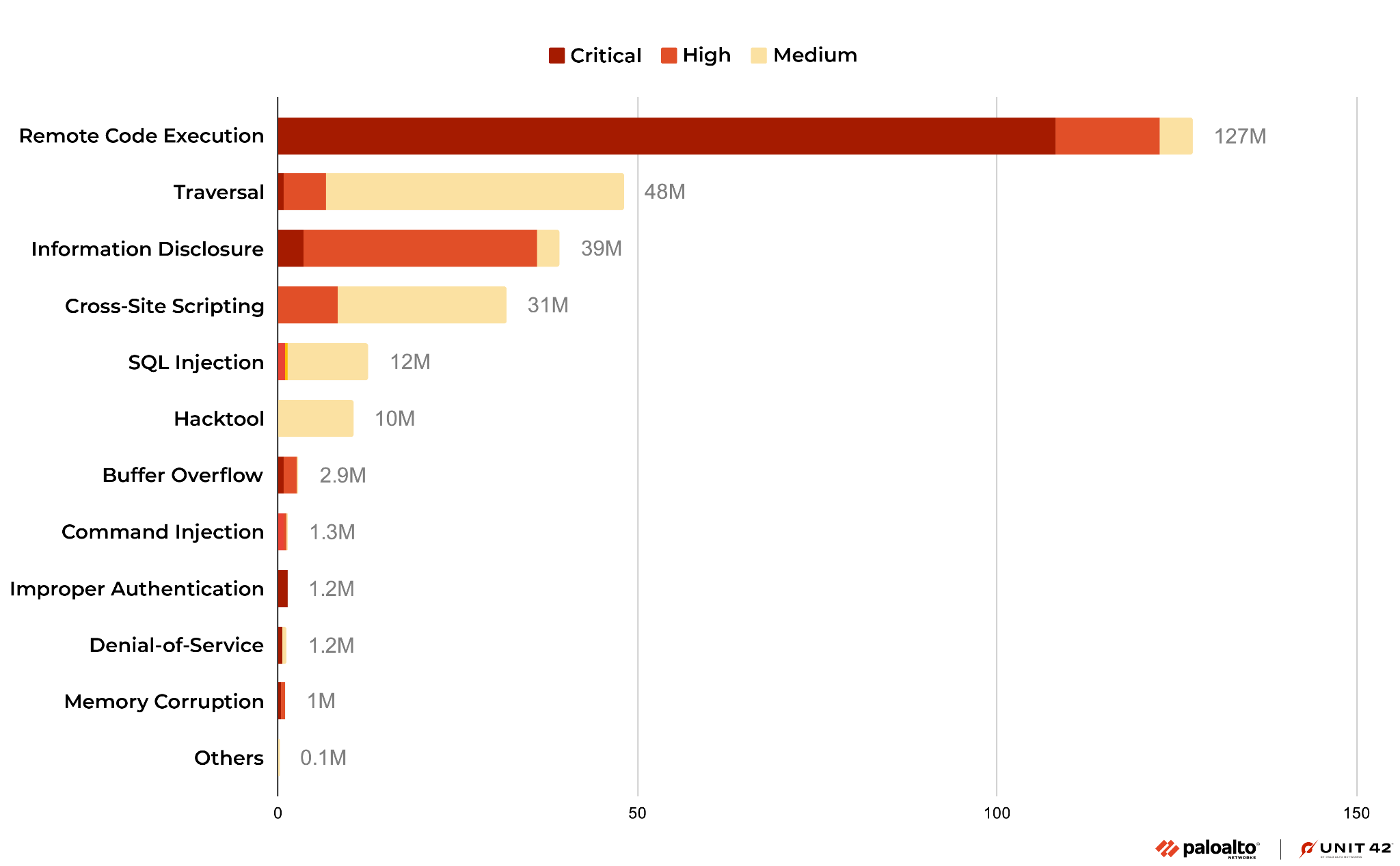
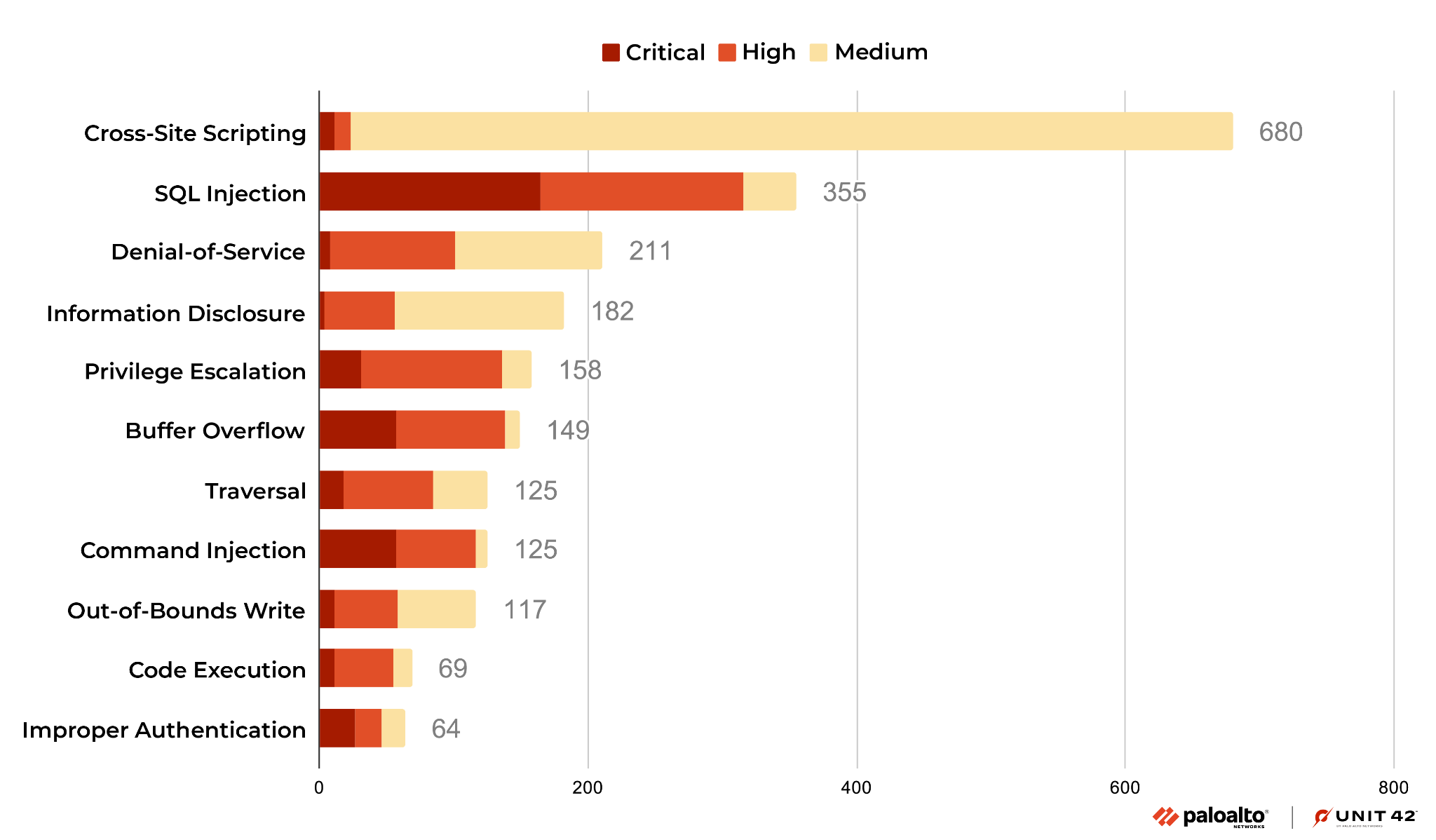
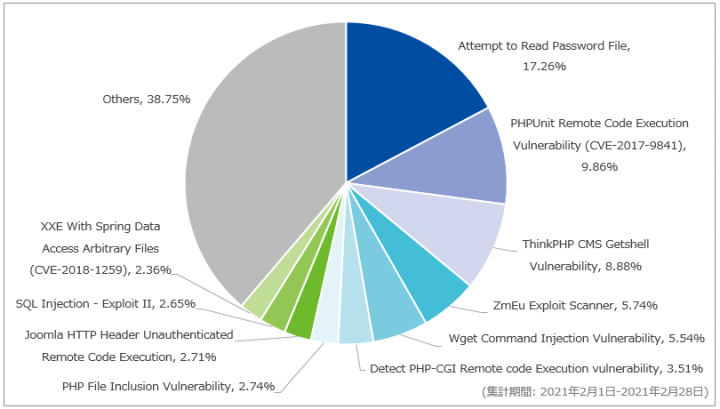
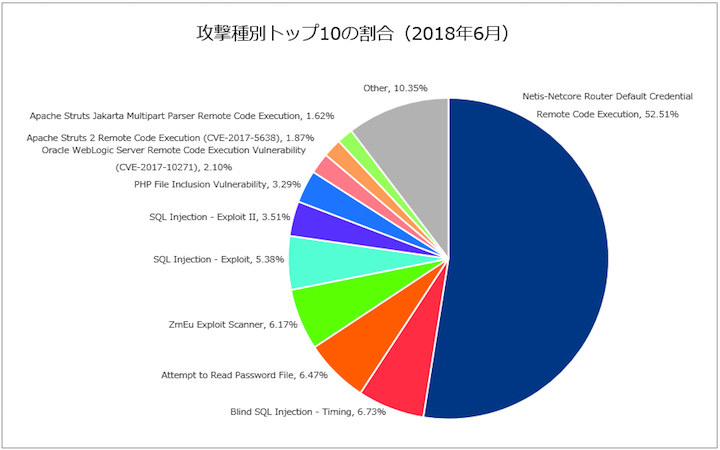
2017 DDoS and Web Application Attack Landscape - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.
![Network slice-based security in mobile networks Patent Grant Verma , et al. March 9, 2 [Palo Alto Networks, Inc.] Network slice-based security in mobile networks Patent Grant Verma , et al. March 9, 2 [Palo Alto Networks, Inc.]](https://uspto.report/patent/grant/10944796/US10944796-20210309-D00011.png)
Network slice-based security in mobile networks Patent Grant Verma , et al. March 9, 2 [Palo Alto Networks, Inc.]